This Item Ships For Free!
Trojan detector online
Trojan detector online, FoxBlade Trojan Detection Microsoft Reveals New Destructive Malware Targeting Ukrainian Infrastructure SOC Prime online
4.97
Trojan detector online
Best useBest Use Learn More
All AroundAll Around
Max CushionMax Cushion
SurfaceSurface Learn More
Roads & PavementRoads & Pavement
StabilityStability Learn More
Neutral
Stable
CushioningCushioning Learn More
Barefoot
Minimal
Low
Medium
High
Maximal
Product Details:
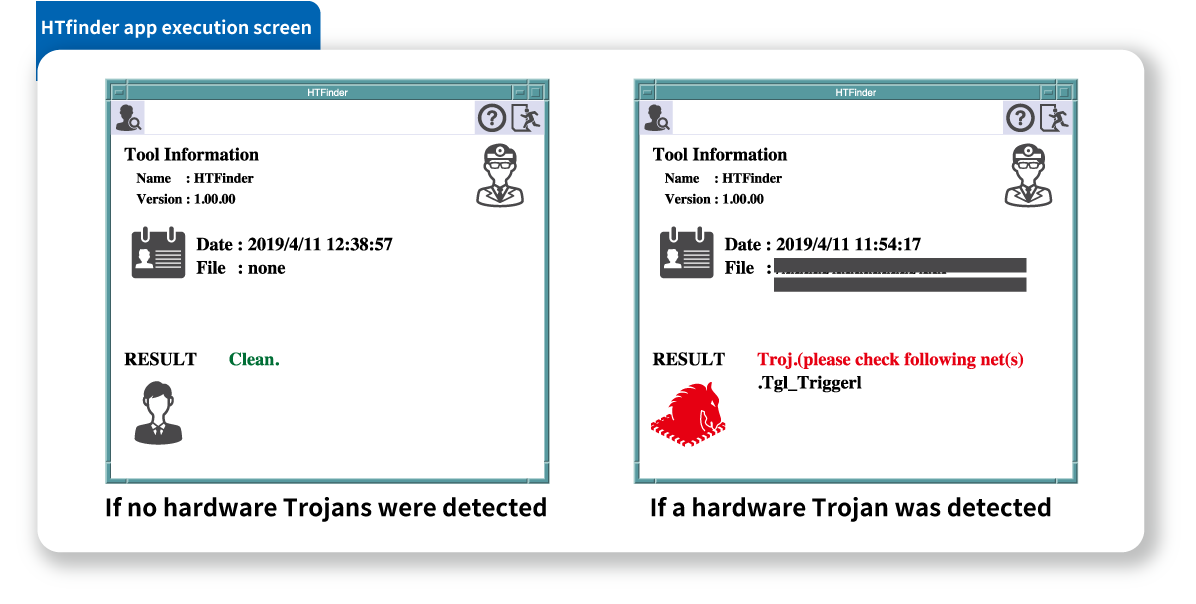
Product Name: Trojan detector onlineQakBot Trojan Detector for ArcSight is released SOC Prime online, TrojanDetector A Multi Layer Hybrid Approach for Trojan Detection in Android Applications online, The hardware Trojan detection service Toshiba Information Systems Japan Corporation online, Download Free Trojan Scanner Cleaner Remover Tool online, Intelligent Electromagnetic Sensors for Non Invasive Trojan Detection online, Hardware Trojan Power EM Side Channel dataset IEEE DataPort online, Trojan detection solution using machine learning online, Trojan Remover online, Classification of hardware Trojan detection techniques 5 Download Scientific Diagram online, Hardware Trojan Detection Leveraging a Novel Golden Layout Model Towards Practical Applications Journal of Electronic Testing online, Best Trojan Removal Tools in 2025 online, Hardware Trojan Detection Using Effective Property Checking Method online, Trojan detector 2025 online, Best Free Trojan Virus Removal Solutions You Should Try in 2025 online, Our Trojan detection method combines bottom up Trigger reverse. Download Scientific Diagram online, Modular Remote Access Trojan Uses Sophisticated Techniques to Evade Detection online, Trojan Remover Windows Uptodown online, Secure IC on Hardware Trojans Detection Secure IC online, Detection of Hardware Trojan Horses VLSI online, Overview of the proposed machine learning based Trojan detection technique. Download Scientific Diagram online, ATTRACT featured stories a novel holistic approach for hardware trojan detection powered by deep learning HERO ATTRACT Project online, Remote Access Trojan Detection Software RAT Protection Guide DNSstuff online, Hardware Trojan Design and Detection online, Trojan Scanner Gridinsoft Help Center online, Hardware Trojan Detection Method Based on Dual Discriminator Assisted Conditional Generation Adversarial Network Journal of Electronic Testing online, Emotet Malware Trojan Detection and Protection Scan Config Scanning scan configuration Greenbone Community Forum online, What Is a Trojan Horse Virus Definition Prevention and Detection ENP online, Concerning pattern of Trojan detection through the real COD executable r Malwarebytes online, Hardware Trojan Detection Techniques. ATPG automatic test pattern. Download Scientific Diagram online, FoxBlade Trojan Detection Microsoft Reveals New Destructive Malware Targeting Ukrainian Infrastructure SOC Prime online, Best Free Trojan Virus Removal Solutions You Should Try in 2025 online, New Android Trojan SoumniBot Evades Detection with Clever Tricks online, Trojan Remover Windows Uptodown online, The hardware Trojan detection service Toshiba Information Systems Japan Corporation online, How to Train Your Hardware Trojan Detector Reverse Engineering into an Underrated Threat Security Network Munich online.
- Increased inherent stability
- Smooth transitions
- All day comfort
Model Number: SKU#6802724